
HCCC Phish Bowl - Cyber Security

Click here for more information.
View Computer Security Resources on ITS Guides and How-To's
HCCC Cybersecurity Center Cybersecurity Events
ITS Reminder: Keeping Yourself Safe From Phishing
Phishing (pronounced fishing) is an attack that steals your identity to either use your personal information and account or to steal your money. HCCC requires two-factor authentication in our Microsoft 365 and email accounts to protect us from phishing attacks. However, attackers can still access your account if you fall victim to a phishing scam. Phishing is most common via email but can also come from text or instant messages. Here are some key ways to recognize a phishing message:
- Contains urgent call to action or threats
Tip: Whenever you see a message calling for immediate action, take a moment, pause, and look carefully at the message. Are you sure it's real? Slow down and be safe. - The sender is a new or infrequent contact or the message is marked “external.”
- Generic greetings or a formal name (Joseph vs. Joe) are used
- Mismatched email domains - the message comes from a Google address, not “.hccc.edu”, or the domain is misspelled, i.e., “.hcccc.ed", "micosoft.com". "googlle.com"
- Suspicious links or unexpected attachments - whenever unsure, contact the sender via another method to verify. Call the person or send a text message.
If you click a link in an email, text, or instant message, and it leads to a login page, STOP. Do not type your credentials. Do not allow the login with your authenticator. A login page is a huge red flag for a phishing scheme. You can type the URL to log in separately, “portal.office.com” for example, but do not follow the link. If unsure, please contact the Help Desk at 201-360-4310 or itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE. Report suspicious emails with the Phish Alert button or forward them to spamFREEHUDSONCOUNTYCOMMUNITYCOLLEGE.
Latest Security Notice
ITS Warning: Final Notice Action Required to Prevent Account Deactivation
February 24, 2026
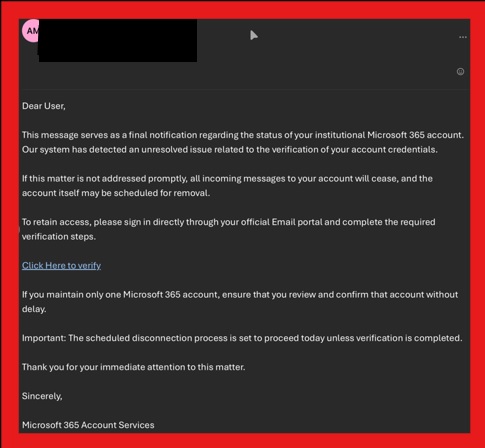
This email is a scam. It is a phishing attempt to gain access to your account, steal your information, and attack other users. Please report it by using the PhishAlert button, forward it to spamFREEHUDSONCOUNTYCOMMUNITYCOLLEGE, or delete it. If you’ve interacted with the email, contact the Help Desk immediately.
February 12, 2026
A phishing scam is currently targeting students. The scam attempts to steal personal information by impersonating official HCCC ITS communications. ITS manages accounts only through the My Access system, not via email or text.
🚨 How the Scam Works
- Fraudulent Email
Students receive an email claiming that their HCCC Microsoft 365 account will be deactivated and are urged to click a link to “verify” it.
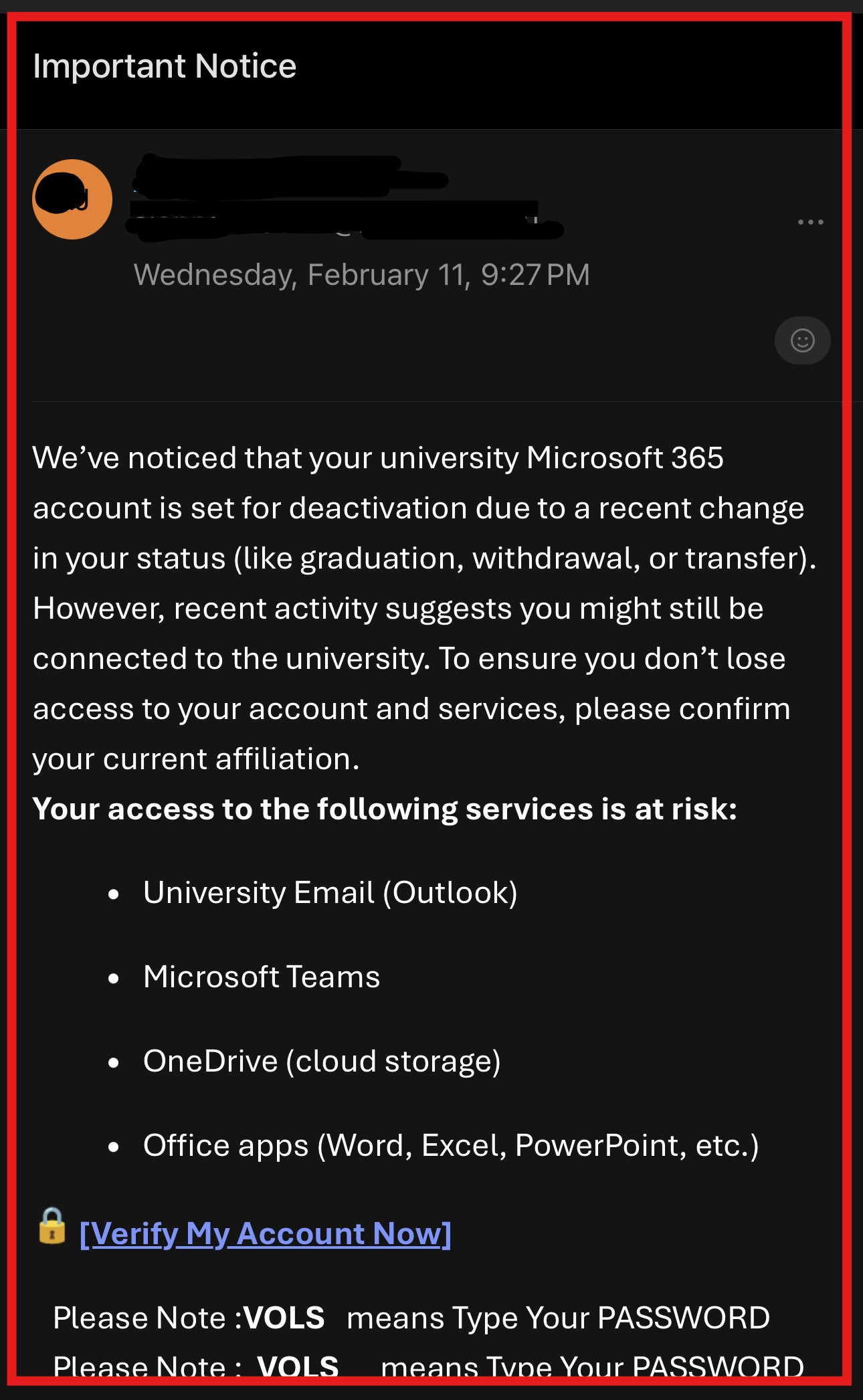
- Phishing Form
The link leads to a fraudulent form that requests youremail, password, and phone number.
- Scam Text Messages
After submitting the form, students may receive text messages impersonating ITS requesting an MFA number to keep the account active.
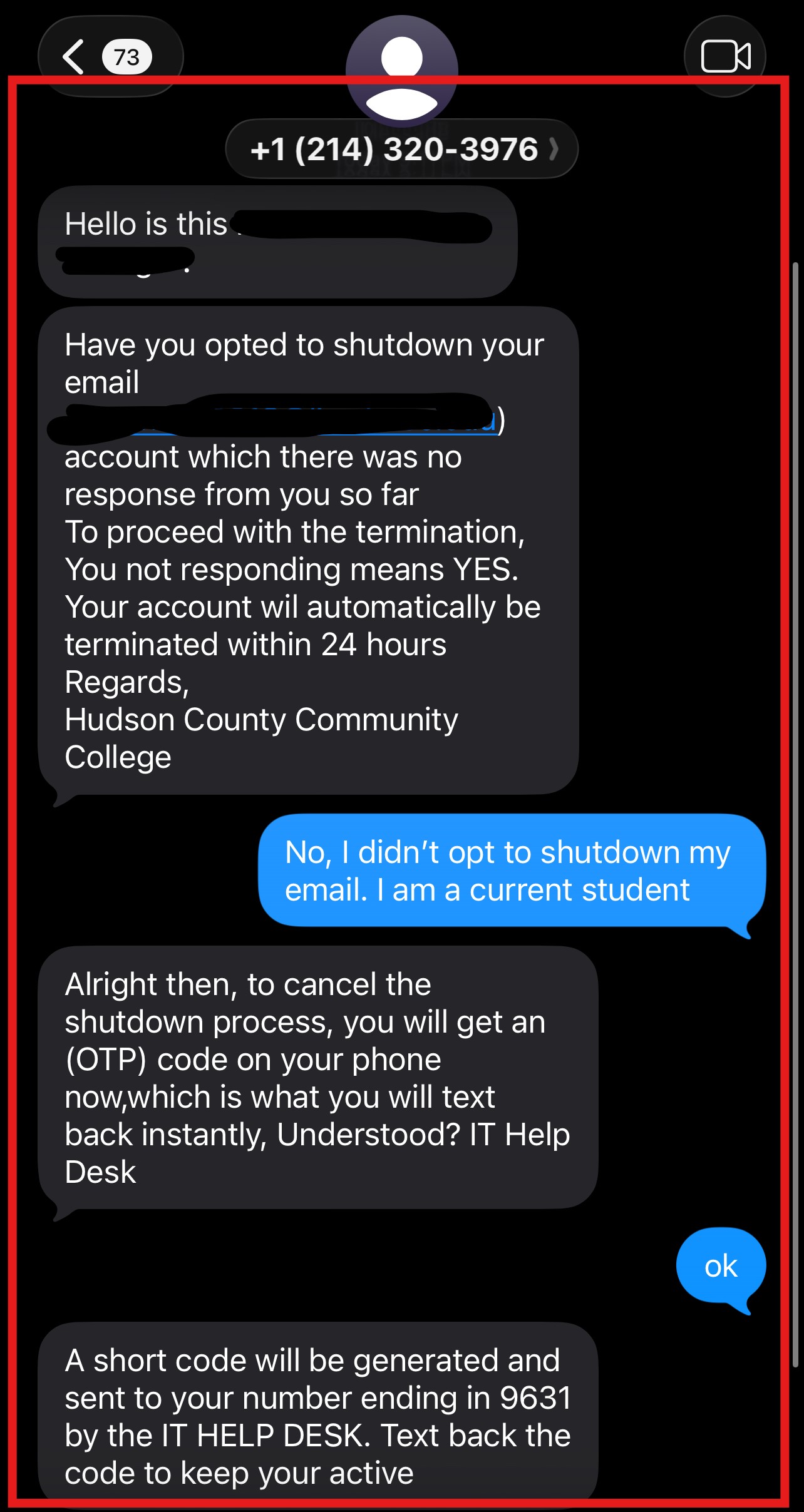
⚠️HCCC ITS will never ask you for MFA authentication.
✅ What You Should Do
- Do not click suspicious links or reply to messages from unknown senders.
- Do not share passwords or verification for a login with anyone else.
- Only enter your password on official HCCC sites (MyAccess, login.hccc.edu) and via your HCCC account on Microsoft.
- If you already responded,change your password immediatelyfrom My Access (https://myaccess.hccc.edu) and contact ITS at itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE.
When in doubt, assume the message is suspicious and report it with the Phish Alert button or by contacting the ITS Help Desk at itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE or (201) 360-4030.
ITS Warning: Are you still enrolled text message
September 26, 2025
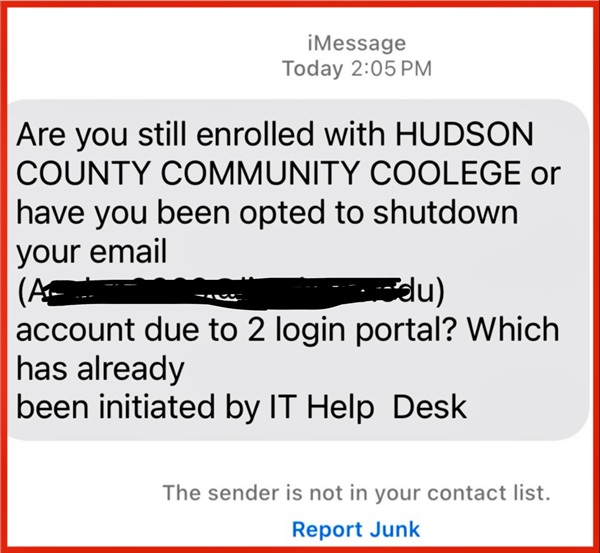
If you have received a similar text message about shutting down your HCCC email, it is a scam. Please report it to your cellular provider and use the PhishAlert button, forward it to spamFREEHUDSONCOUNTYCOMMUNITYCOLLEGE, or delete it. If you’ve interacted with the email, contact the Help Desk immediately.
HCCC Phish Bowl
Phishing generally consists of a link in your email which leads to a fake form or login page.
Cybercrime includes spam, viruses, denial of service attacks, malware (Malicious code), fraud, identity theft, and social engineering attacks.
If you receive a questionable email in your HCCC account, please report it to ITS by forwarding the message to spamFREEHUDSONCOUNTYCOMMUNITYCOLLEGE or use the Phish Alert button in your email. As with all email, if you doubt the contents of a message, call or text the sender and verify that they sent it intentionally.
Though evidence is not always needed when reporting a cybercrime, it is important to keep all records relating to your complaint. Items that should be preserved include:
- Canceled checks
- Certified mail receipts and envelopes
- Money order receipts
- Wire receipts
- Chat room and newsgroup texts
- Credit card receipts
- Facsimiles
- Log files with the date, time, and time zone
- Messages from Facebook, Twitter, and other social networking sites
- Pamphlets and brochures
- Phone bills
- Printed or electronic copies of email messages with full header information
- Printed or electronic copies of web pages
- Reset all passwords of accounts associated with this incident (email, bank, social media accounts).
- Turn on two-factor or multi-factor authentication on all accounts that offer it.
- If you provided any personally identifiable information, you should access https://www.identitytheft.gov/ and complete their checklist for next steps.
- For any financially related fraud:
- Check your bank accounts frequently for unauthorized charges.
- Contact your bank to report all unauthorized transactions.
- Get your free annual credit reports from https://annualcreditreport.com.
- Consider placing a free credit freeze http://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs.
- If you place a freeze, you'll have to lift the freeze before you apply for a new credit card or cell phone - or any service that requires a credit check.
- If you decide not to place a credit freeze, at least consider placing a fraud alert http://www.consumer.ftc.gov/articles/0497-credit-freeze-faqs#difference.
- If you gave a scammer your Social Security Number, file your taxes as quickly as possible, before the scammer can.
If you are the victim of a cybercrime, you should report the situation as soon as you find out about it. There are several resources available to you.
New Jersey residents are encouraged to report all cyber incidents to the NJCCIC's
Cyber Liaison Officers:
Email: njccic@cyber.nj.gov
Phone: 866-4-SAFE-NJ or 211
Website: https://www.cyber.nj.gov/report/
For more information on how the NJCCIC can help New Jersey's cyberattack victims,
visit the NJCCIC's website at:
https://www.cyber.nj.gov/

The Federal Trade Commission (FTC) operates the Consumer Sentinel, a secure online database used by civil and law enforcement
agencies worldwide to expose patterns of cybercrime. You can file a complaint at:
https://reportfraud.ftc.gov/
In cases of identity theft, call the FTC hotline at 1-877-IDTHEFT or visit:
https://identitytheft.gov
Regardless of whether the cybercrime takes place over multiple jurisdictions, your local police department must take a formal report and refer the case to other agencies, when appropriate. Some local agencies have departments that focus specifically on cybercrime.
The Internet Crime Complaint Center (IC3) is a partnership between the FBI and the National White Collar Crime Center. IC3 reviews complaints related to cybercrime and refers them to the appropriate agencies.
You can file a complaint online at:
https://www.ic3.gov/
The Better Business Bureau investigates disagreements between businesses and customers.
You can file a complaint online at:
https://www.bbb.org/file-a-complaint
The U.S. Postal Inspection Service investigates fraudulent online auctions and other cases involving the mail.
You can file a complaint online at:
https://www.uspis.gov/
How can you tell if an e-mail message is a fraud?
Attackers use different methods of deception as phishing strategies. They create fake messages and websites, that imitate the original ones. With their help, they will try to lure you into handing over your personal information. The messages will ask you to reply to them, follow a link included in the message or download an attachment. The communication appears to be initiated by a legitimate person or company. Famous phishing attacks imitate messages from financial institutions, government agencies, online retailers and services, social networks, or even from a friend or colleague.
To make phishing look genuine, attackers include photos and information from the original website. They may even redirect you to the company’s website and collect the data through a false pop-up window. Or it can happen the other way around: the attacker first requests your personal data, then redirects you to the real website. Other times, the message tells you that you have been targeted by a scam and that you urgently need to update your information in order to keep your account safe.
- Requests for personal information in an e-mail message.
Most legitimate businesses have a policy that they do not ask you for your personal information through e-mail. Be very suspicious of a message that asks for personal information even if it might look legitimate. - Urgent wording.
Wording in phishing e-mail messages is usually polite and accommodating in tone. It almost always tries to get you to respond to the message or to click the link that is included. To increase the number of responses, criminals attempt to create a sense of urgency so that people immediately respond without thinking. Usually, fake e-mail messages are NOT personalized, while valid messages from your bank or e-commerce company generally are. - Fake links.
Phishers are getting very sophisticated in their ability to create misleading links to the point where it is impossible for the average person to tell if the link is legitimate or not. It’s always best to type in the Web address or URL you know is correct into your browser. Also you can save the correct URL to your browser “Favorites.” Do not copy and paste URLs from messages into your browser. Some of the techniques that criminals have used in the past to fake links are as follows: - Message body is an image not text.
To avoid detection by spam filters, fake e-mail messages used in phishing schemes often use an image instead of text in the message body. If the sent spam message uses real text, the Outlook Junk E-mail Filter will very likely move the message to the Junk E-mail folder. The message body image is usually a hyperlink, you can tell because when you rest the pointer on the message body, the pointer becomes a hand. - Promises that seem too good to be true.
Use common sense and be suspicious when you are offered money or discounts that seem too good to be true.
- Never reply to e-mail messages that request your personal information.
Be very suspicious of any e-mail message from a business or person that asks for your personal information - or one that sends you personal information and asks you to update or confirm it. - Don’t click links in suspicious e-mail.
Don’t click a link contained in a suspicious message. Instead, visit Web sites by typing their URL into your browser or by using your Favorites link. Do not copy and paste links from messages into your browser. - Change your password regularly or if you suspect any compromise.
Once you have made the password change notify the provider of the service/account in question directly regarding the possibility of fraud or compromise. - Don’t send personal information in regular e-mail messages.
Regular e-mail messages are not encrypted and are like sending a post card, anyone whose hands it passes through can read its content. - Do business only with companies you know and trust.
A legitimate business Web site should always have a privacy statement that specifically states that the business won’t pass your name and information to other people. - Make sure the Web site uses encryption when personal information is being transacted.
The Web address should be preceded by https:// instead of the usual http:// in the browser’s address bar. Also, double-click the lock icon on your browser’s status bar to display the digital certificate for the site. The name that follows “Issued to” in the certificate should match the site that you think you’re on. If you suspect that a Web site is not what it should be, leave the site immediately and report it. Don’t follow any of the instructions it presents. - Monitor your transactions.
Review your order confirmations and credit card and bank statements as soon as you receive them to make sure that you’re being charged only for transactions you made. Immediately report any irregularities in your accounts by dialing the number shown on your account statement. Using just one credit card for online purchases makes it easier to track your transactions. - Use credit cards for transactions on the Internet.
In most locales, your personal liability in case someone compromises your credit card is significantly limited. By contrast, if you use direct debit from your bank account or a debit card, your personal liability frequently is the full balance of your bank account. In addition, a credit card with a small credit limit is preferable for use on the Internet because it limits the amount of money that a thief can steal in case the card is compromised. Better yet, several major credit card issuers are now offering customers the option of shopping online with virtual, single-use credit card numbers, which expire within one or two months. For more details, ask your bank about perishable virtual credit card numbers.

Phish Bowl Categories
Fraudulent emails and scams that relate to job opportunities and work study.
For legitimate job postings, visit Job Opportunities.
You can also visit Career Pathways for additional resources.
Contact Information
Information Technology ServicesJournal Square Campus
Patricia Clay
Associate Vice President for Technology and Chief Information Officer
70 Sip Avenue - 3rd Floor
Jersey City, NJ 07306(201) 360-4310
itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE
computerlabsFREEHUDSONCOUNTYCOMMUNITYCOLLEGE
North Hudson Campus
4800 John F. Kennedy Blvd - 3rd Floor
Union City, NJ 07087(201) 360-4309
itshelpFREEHUDSONCOUNTYCOMMUNITYCOLLEGE






